./18-Apr-2021 17:07 - ChangeLog 18-Apr-2021 05 DJM-GPG-KEY.asc 17-Sep-2002 INSTALL 18-Apr-2021 17:07. NVD Analysts use publicly available information to associate vector strings and CVSS scores. We also display any CVSS information provided within the CVE List from the CNA.
OpenSSH is a free opensource version of the SSH connectivity tools. OpenSSH encrypts all traffic (including passwords) to effectively eliminate eavesdropping, connection hijacking, and other attacks unlike Telnet,rlogin or ftp where the data is not encrypted and transmitted in plain text. Additionally, OpenSSH provides secure tunneling capabilities and several authentication methods, and supports all SSH protocol versions.
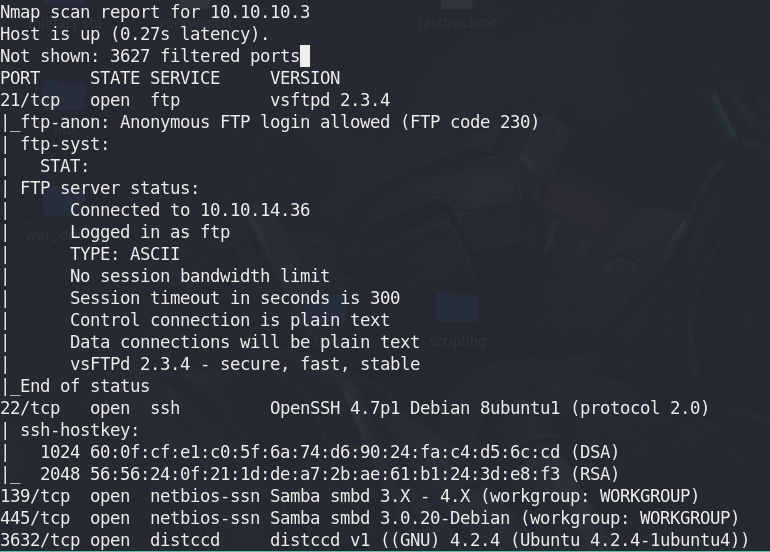
Solaris 10 is by default installed with SSH server and the clients. However, if you have chosen to ignore SSH at the time of installation or have started the install with a minimal install then you may need to install OpenSSH manually.
The easiest way to install OpenSSH in Sun Solaris is to use the pre-compiled packages from sunfreeware.
The following are the packages that are required to be installed for OpenSSH to work properly in Solaris 10:
To start of, download the packages from the following sunfreeware.com links for sun solaris 10 Sparc:
gcc
Zlib
OpenSSL
OpenSSH
Once done, upload the files onto the server so we can start to unzip the files and install.
Unzip and install gcc
solaris10# gunzip libgcc-3.4.6-sol9-sparc-local.gz
solaris10# pkgadd -d libgcc-3.4.6-sol9-sparc-local
…
…
Installation of <SMCgcc> was successful.

Unzip and install zlib
solaris10# gunzip zlib-1.2.1-sol9-sparc-local.gz
solaris10# pkgadd -d zlib-1.2.1-sol9-sparc-local
…
…
Installation of <SMCzlib> was successful.
Unzip and install OpenSSL
solaris10# gunzip openssl-0.9.8f-sol9-sparc-local.gz
solaris10# pkgadd -d openssl-0.9.8f-sol9-sparc-local
…
…
Installation of <SMCossl> was successful.
Unzip and install OpenSSH
solaris10# gunzip openssh-4.7p1-sol9-sparc-local.gz
solaris10# pkgadd -d openssh-4.7p1-sol9-sparc-local
The packages are now installed. All fuses.
Create /var/empty directory
solaris10# mkdir /var/empty
Change directory ownership to Root user and sys group

solaris10# chown root:sys /var/empty
Change permissions
solaris10# chmod 755 /var/empty
Add sshd user & group
solaris10# groupadd ssh
Blackweb keyboard wasd. solaris10# # useradd -g sshd -c ‘sshd privsep’ -d /var/empty -s /bin/false sshd
Edit the default /usr/local/sshd_config file and make the following changes:
Replace the line
Subsystem sftp /usr/libexec/sftp-server
with
Subsystem sftp /usr/local/libexec/sftp-server
Generate Keys for the server
solaris10# ssh-keygen -t rsa1 -f /usr/local/etc/ssh_host_key -N “”
solaris10# ssh-keygen -t dsa -f /usr/local/etc/ssh_host_dsa_key -N “”
solaris10# ssh-keygen -t rsa -f /usr/local/etc/ssh_host_rsa_key -N “”
Enable OpenSSH server daemon sshd to run at the system startup
Edit /lib/svc/method/sshd file and change the path for the SSH DIR, KEYGEN & the start daemon as follows:
SSHDIR=/usr/local/etc/ssh
KEYGEN=”/usr/local/bin/ssh-keygen -q”
‘start’)
/usr/local/sbin/sshd
That is it. All done and ready to go. Try connecting to the server using a ssh client like PUTTY.
This tutorial will help you create an automatic backup on dropbox for your server.
Warning: This tutorial is for OpenSSH version 4.x only.
PLEASE update to 5.0(or newer). If you have 6.x, head here to get the tutorial for the update. Its much easier.
Story time: I run one web server with 5 users. I wasn't really interested in allowing them to see the systems (and my personal) files even if they couldn't edit them. I posted a question about what to do on codingforums.com. The tutorial I was given there seemed faulty hence my post on linuxquestions.org. I eventually found several tutorials and got it to work. Here is a tutorial that is really a mix or several other tutorials and tips I have found on the net in my epic search.
NOTE: This tutorial is for attempting to jail users to their home directory and allowing them ONLY sftp access.
NOTE: This works and has been tested on centos 4.4
What does this do again..?
This will majorly increase security for a multi-user server. The main things it does are:
Lock users to their home directory
--This blocks their eyes from the rest of your system and from files like: system binaries, other users' files, backups, configuration files
Disable regular ssh access
--Many users just having a web site won't need an actual command interface. Its just one more thing to be hacked.
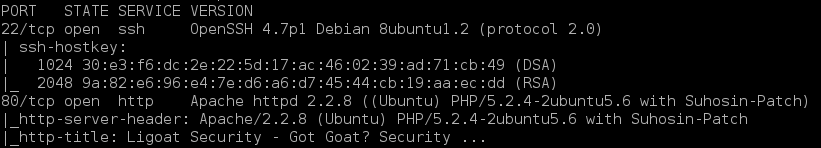
Openssh 4.7p1 Metasploit
FTP already does this!!! right?
Yes, but your forgetting one thing.. this is SFTP!!! It's encrypted and so it is much harder for hackers to sniff packets. Also, the user management is at the system level, so your server tells users what they can and can't do. If your FTPd runs as root or with a high permissions level and a ftp user hacks it, it means they have root or at least high permissions over the ENTIRE server? Not anymore.
The Tutorial
Warning: This tutorial is for OpenSSH version 4.x only.
PLEASE update to 5.0(or newer). If you have 6.x, head here to get the tutorial for the update. Its much easier.
Openssh 4.7 P1 Exploit
This tutorial uses the /opt directory to install the necessary dependences. If you wish to install them anywhere else or do not have an opt directory on your server you may do so, but make sure to change all the paths in the code below. All commands must be run as root
NOTE: The jailing setup for OpenSSH ver5 is much cleaner and uses less hacks then ver4. If you need to jail users, make sure to update to version 5.
NOTE: This setup is meant for installing on a fresh server. If you already have configuration files for the programs we will be installing (zlib,openssl, and openssh), they will not be overwritten, but you will have to copy them from their old paths to the paths you install with here (recommended: /opt/..).
- You need the GNU Compiler Collection to install these programs. When it asks you if you want to proceed reply with a 'y'.
- Install zlib
- Now we install openssl into the opt directory as well The make commands here take forever to run.
- Next we will download openssh
- Now we have to replace the sftp-server.c file(in the openssh-4.7p1 folder) with this one: sftp-server.c
- Now we will install openssh. To find your xauth file is located you may need to run the 'which xauth' command. If you know what you are doing you may add your own options to the configure command below. Some of these commands make take some time to run. Go grab a coke.
REMEMBER: This tutorial is meant for setting up a server for the first time. You may need to copy your sshd_config file (or at least the directives you want to keep) from /etc/ssh to save your old settings. - To automatically run the new ssh shell, we will use init. You need to change the following lines in /etc/init.d/sshd Then we will restart ssh and test to see if it is running smoothly. The telnet command should return some lines looking like this: You need to be sure that the last line includes the 'OpenSSH_4.7' to confirm that it is the version we jsut installed.
- The sftp-server file needs to be run with root privileges.
- Download the sftpsh shell to your /opt directory. Then edit the following lines in that file.
- We will compile the new shell, move it to the system path, and add it to the shells file.
- You're all set.
- Set all users shell (NOT ROOT'S!!!) to /bin/sftpsh.
- Set the users new home directories using our chroot token.
Example: /home/username/./
This will make the user see '/home/username/' as just '/' with no ability to see any higher in the directory tree.
- Now test. Try to login with putty (or any terminal) and see what happens(you should get a nice error). Then try to login with WinSCP or another SFTP transfer program. You should start in a directory called '/' and only be able to see and edit your own files.
NOTICE: Yum will not update these programs anymore (zlib,openssl,openssh). When a new version comes out, you will have to make your own install from a tarball again. Just follow the same directions.
Credits




